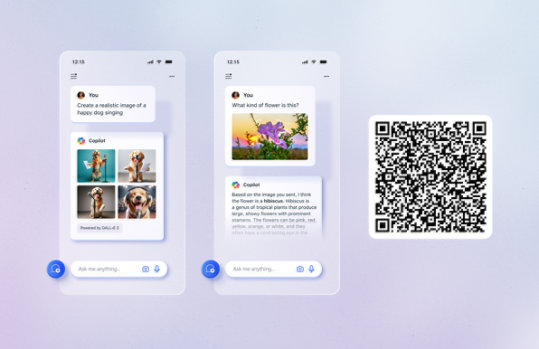
Unlock your potential with Microsoft Copilot
Get things done faster and unleash your creativity with the power of AI anywhere you go.
Internet Explorer 6 Retired Content
The content you requested has already retired. It's available to download on this page.
Important! Selecting a language below will dynamically change the complete page content to that language.
Version:
1.0
Date Published:
7/18/2016
File Name:
IE6_en-us.pdf
File Size:
5.4 MB
Internet Explorer 6 content, including the Internet Explorer 6 Administration Kit Service Pack 1: Deployment Guide and the Microsoft Internet Explorer 6 Resource Kit, which includes technical detail, insider insights, and must-have tools—including the Internet Explorer Administration Kit (IEAK).Supported Operating Systems
Windows 2000, Windows NT, Windows XP
Windows NT, Windows 2000, or Windows XP- The download is a pdf file. To start the download, click Download.
- If the File Download dialog box appears, do one of the following:
- To start the download immediately, click Open.
- To copy the download to your computer to view at a later time, click Save.
