Events
Apr 29, 2 PM - Apr 30, 7 PM
Join the ultimate Windows Server virtual event April 29-30 for deep-dive technical sessions and live Q&A with Microsoft engineers.
Sign up nowThis browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
In Windows Server 2016, you can use an Access Control Policy to create a rule that will permit or deny users based on an incoming claim. In Windows Server 2012 R2, using the Permit or Deny Users Based on an Incoming Claim rule template in Active Directory Federation Services (AD FS), you can create an authorization rule that will grant or deny user's access to the relying party based on the type and value of an incoming claim.
For example, you can use this to create a rule that will permit only users that have a group claim with a value of Domain Admins to access the relying party. If you want to permit all users to access the relying party, use the Permit Everyone Access Control Policy or the Permit All Users rule template depending on your version of Windows Server. Users who are permitted to access the relying party from the Federation Service may still be denied service by the relying party.
You can use the following procedure to create a claim rule with the AD FS Management snap-in.
Membership in Administrators, or equivalent, on the local computer is the minimum required to complete this procedure. Review details about using the appropriate accounts and group memberships at Local and Domain Default Groups.
In Server Manager, click Tools, and then select AD FS Management.
In the console tree, under AD FS, click Access Control Policies.
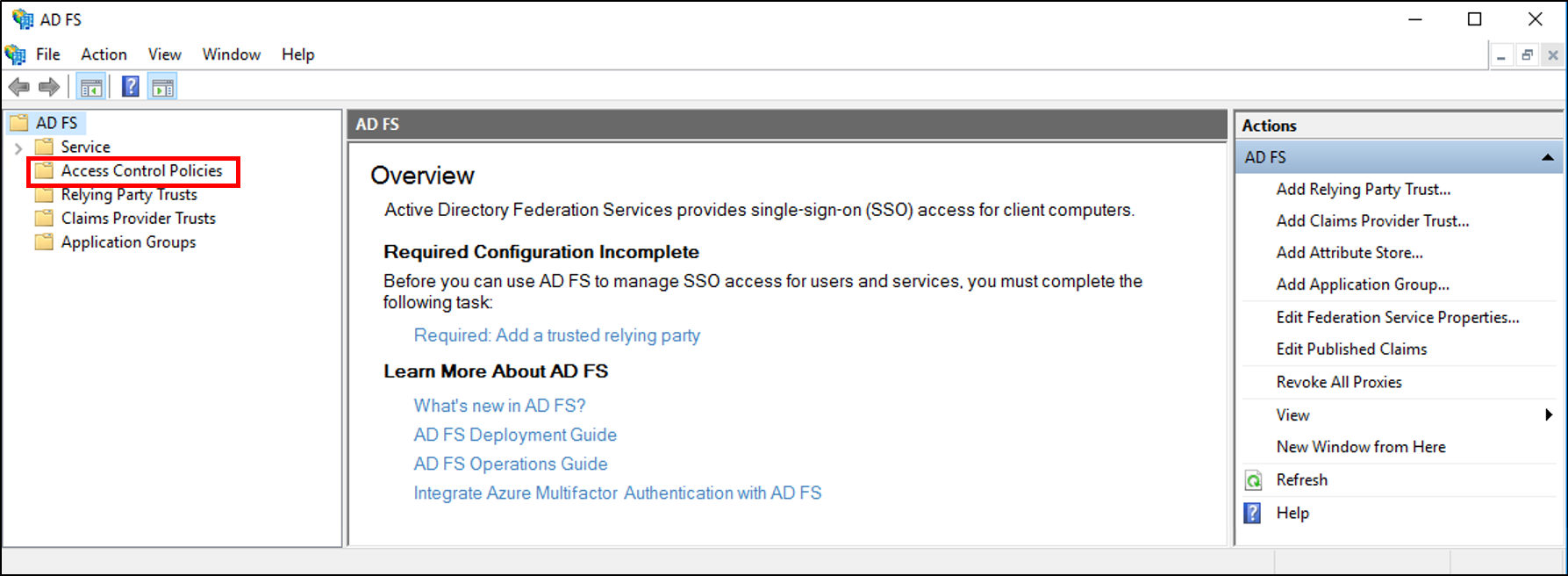
Right-click and select Add Access Control Policy.
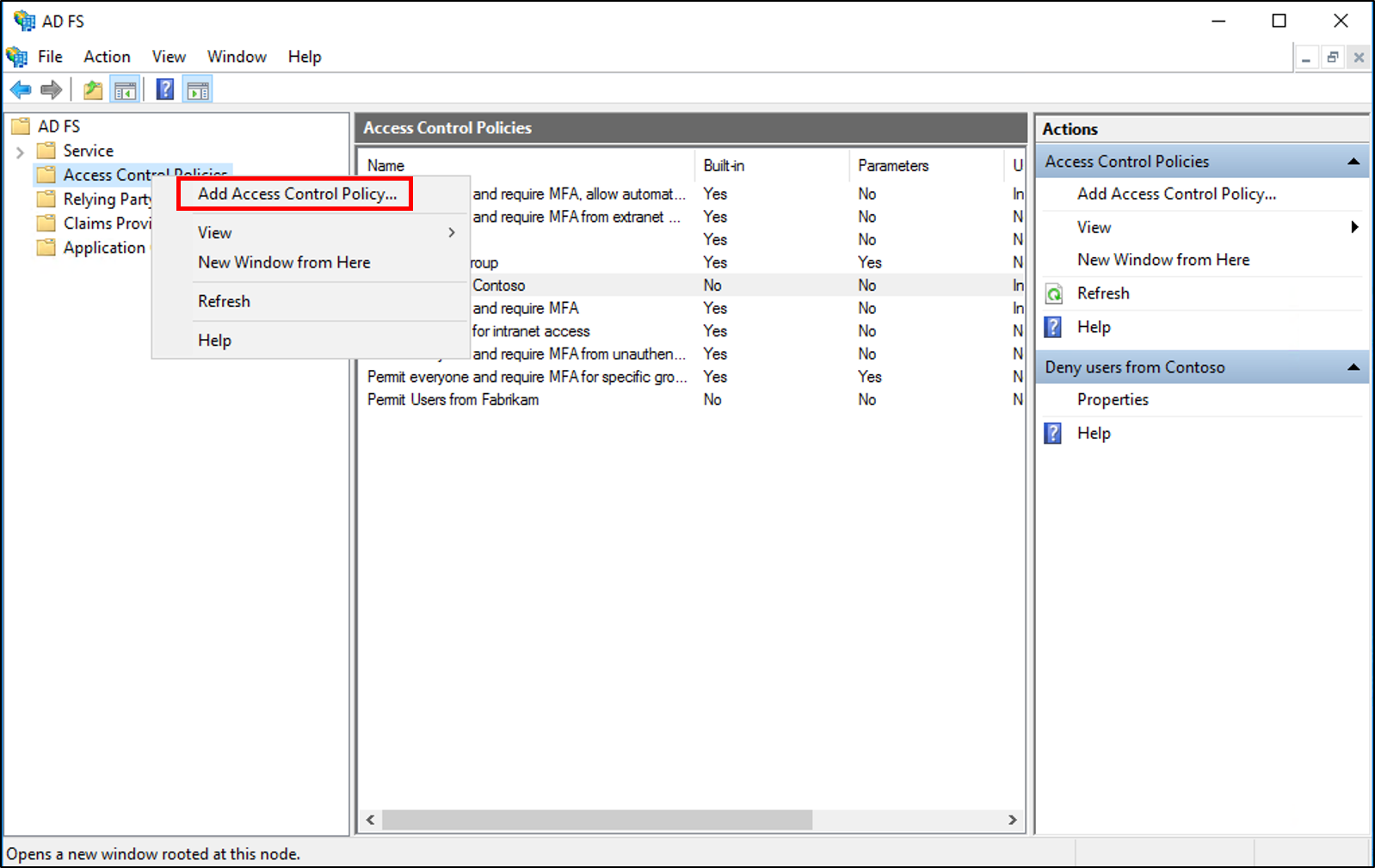
In the name box, enter a name for your policy, a description and click Add.
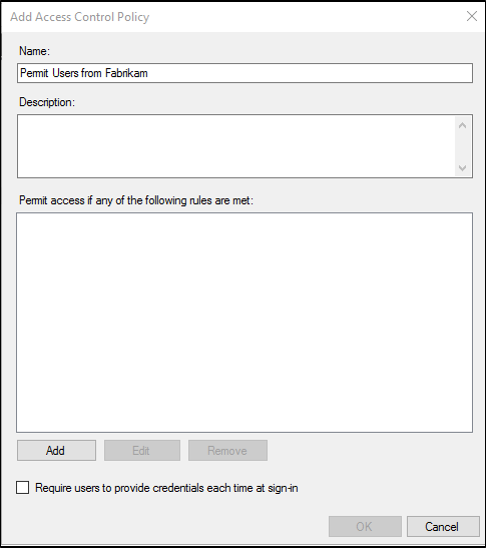
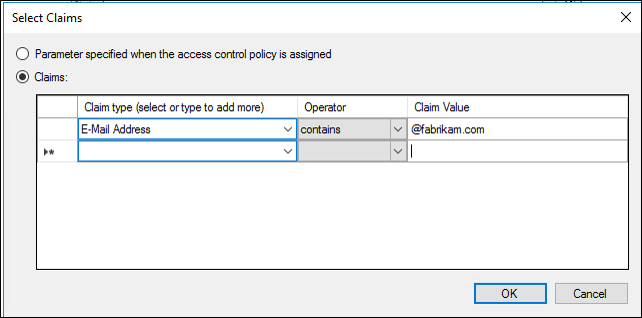
On the Rule Editor, under users, place a check in with specific claims in the request and click the underlined specific at the bottom.
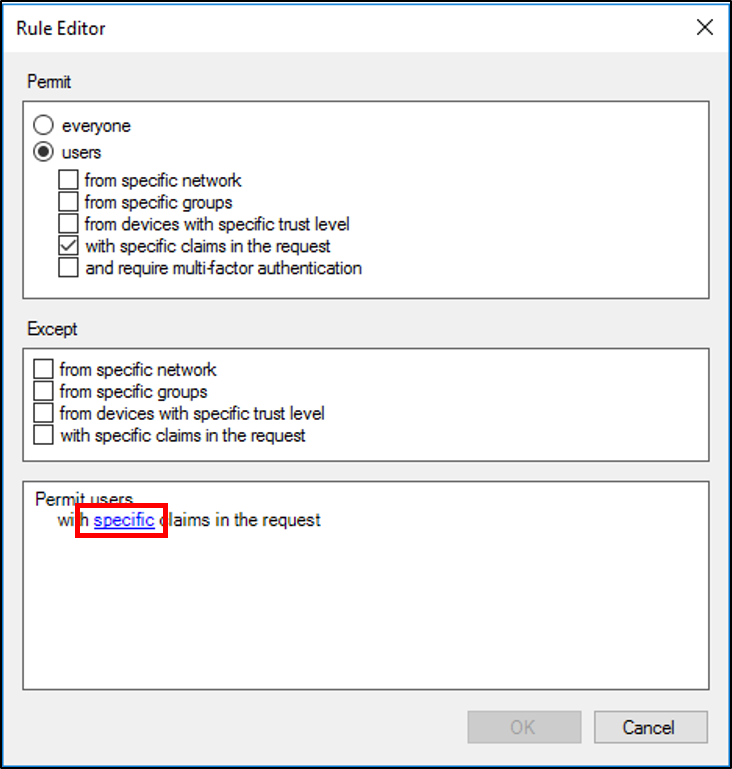
On the Select Claims screen, click the Claims radio button, select the Claim type, the Operator, and the Claim Value then click Ok.
On the Rule Editor click Ok. On the Add Access Control Policy screen, click Ok.
In the AD FS Management console tree, under AD FS, click Relying Party Trusts.
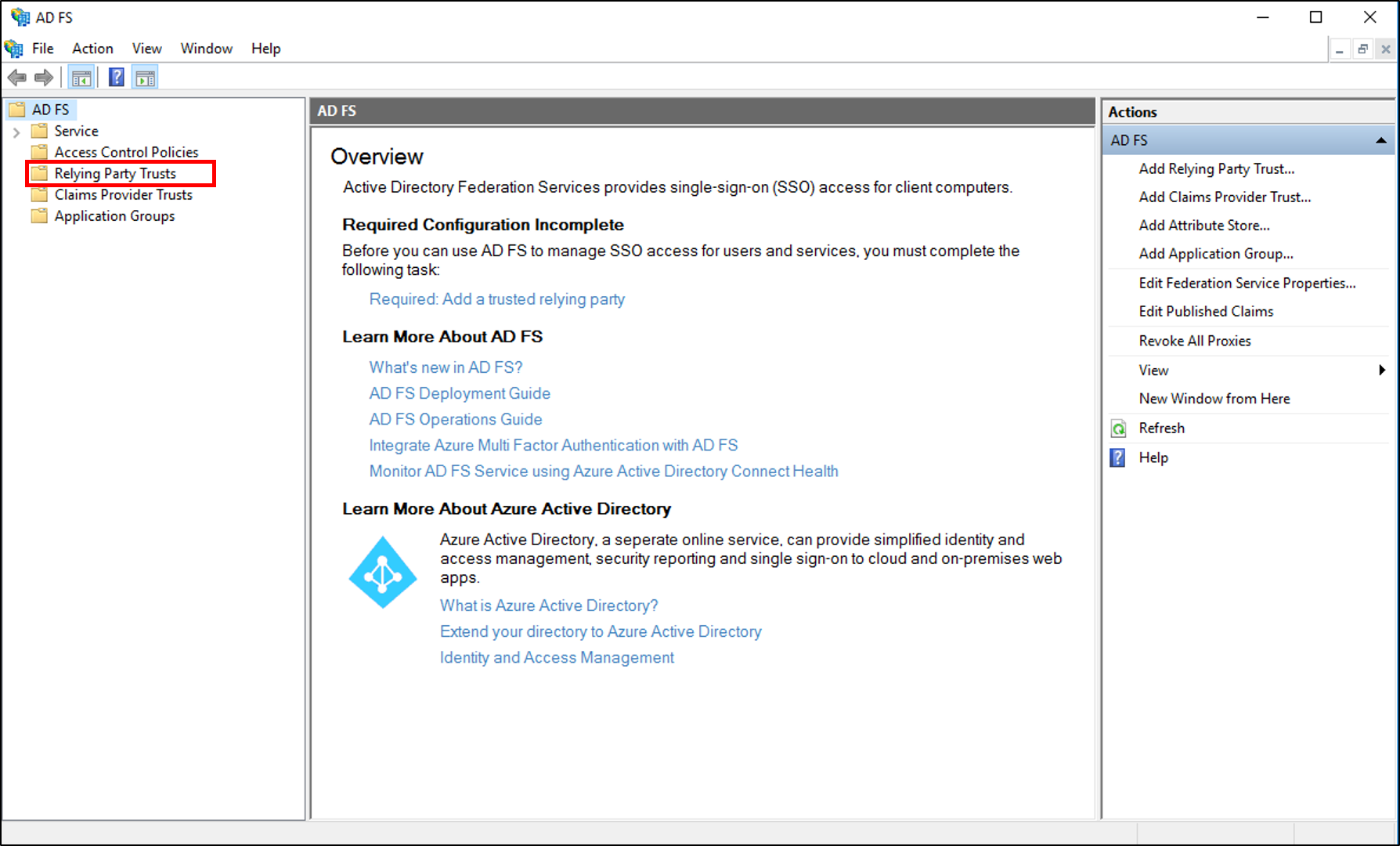
Right-click the Relying Party Trust that you want to permit access to and select Edit Access Control Policy.
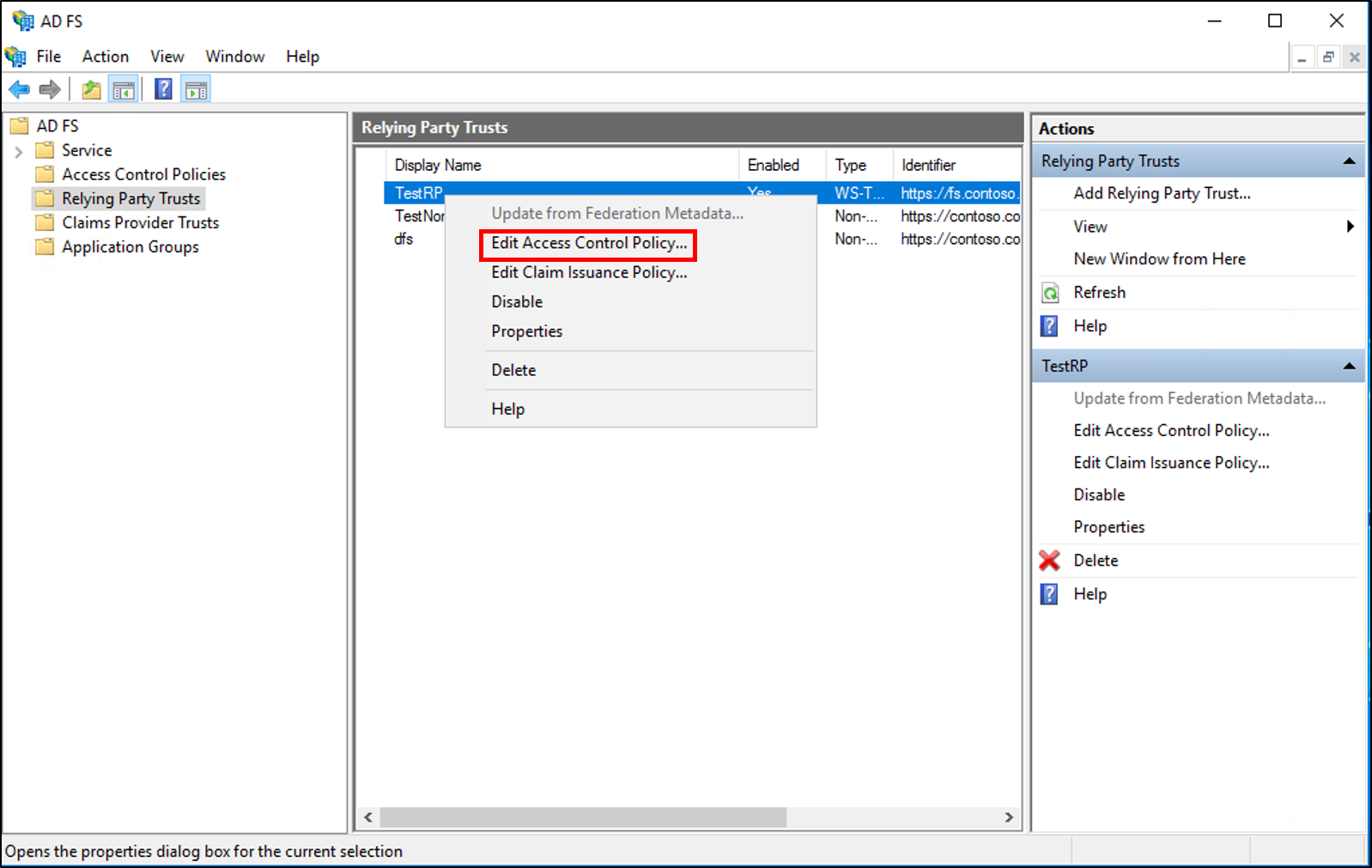
On the Access control policy select your policy and then click Apply and Ok.
In Server Manager, click Tools, and then select AD FS Management.
In the console tree, under AD FS, click Access Control Policies.

Right-click and select Add Access Control Policy.

In the name box, enter a name for your policy, a description and click Add.
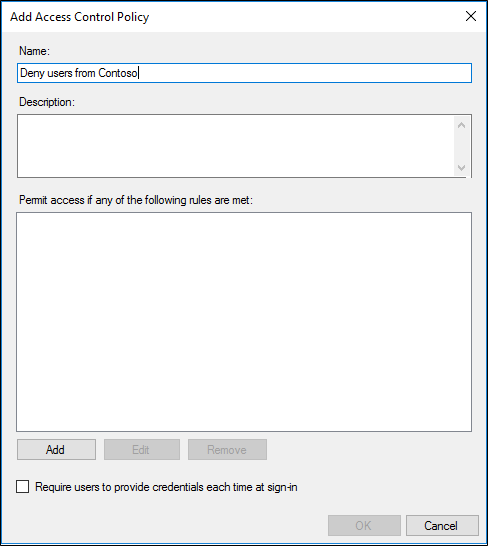
On the Rule Editor, make sure everyone is selected and under Except place a check in with specific claims in the request and click the underlined specific at the bottom.
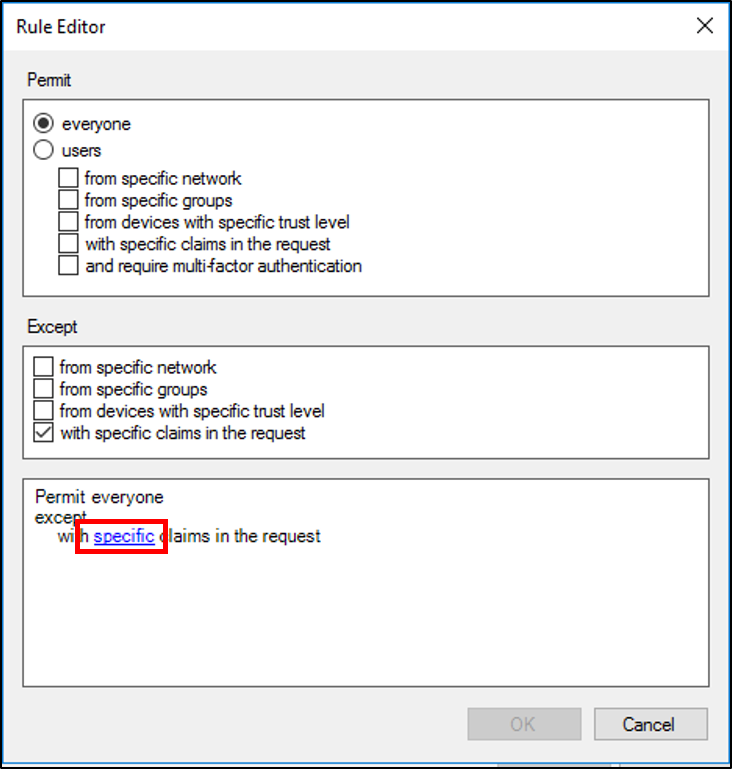
On the Select Claims screen, click the Claims radio button, select the Claim type, the Operator, and the Claim Value then click Ok.
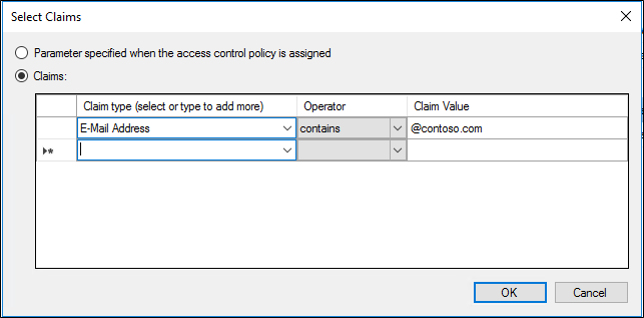
On the Rule Editor click Ok. On the Add Access Control Policy screen, click Ok.
In the AD FS Management console tree, under AD FS, click Relying Party Trusts.

Right-click the Relying Party Trust that you want to permit access to and select Edit Access Control Policy.

On the Access control policy select your policy and then click Apply and Ok.
In Server Manager, click Tools, and then select AD FS Management.
In the console tree, under AD FS\Trust Relationships\Relying Party Trusts, click a specific trust in the list where you want to create this rule.
Right-click the selected trust, and then click Edit Claim Rules.
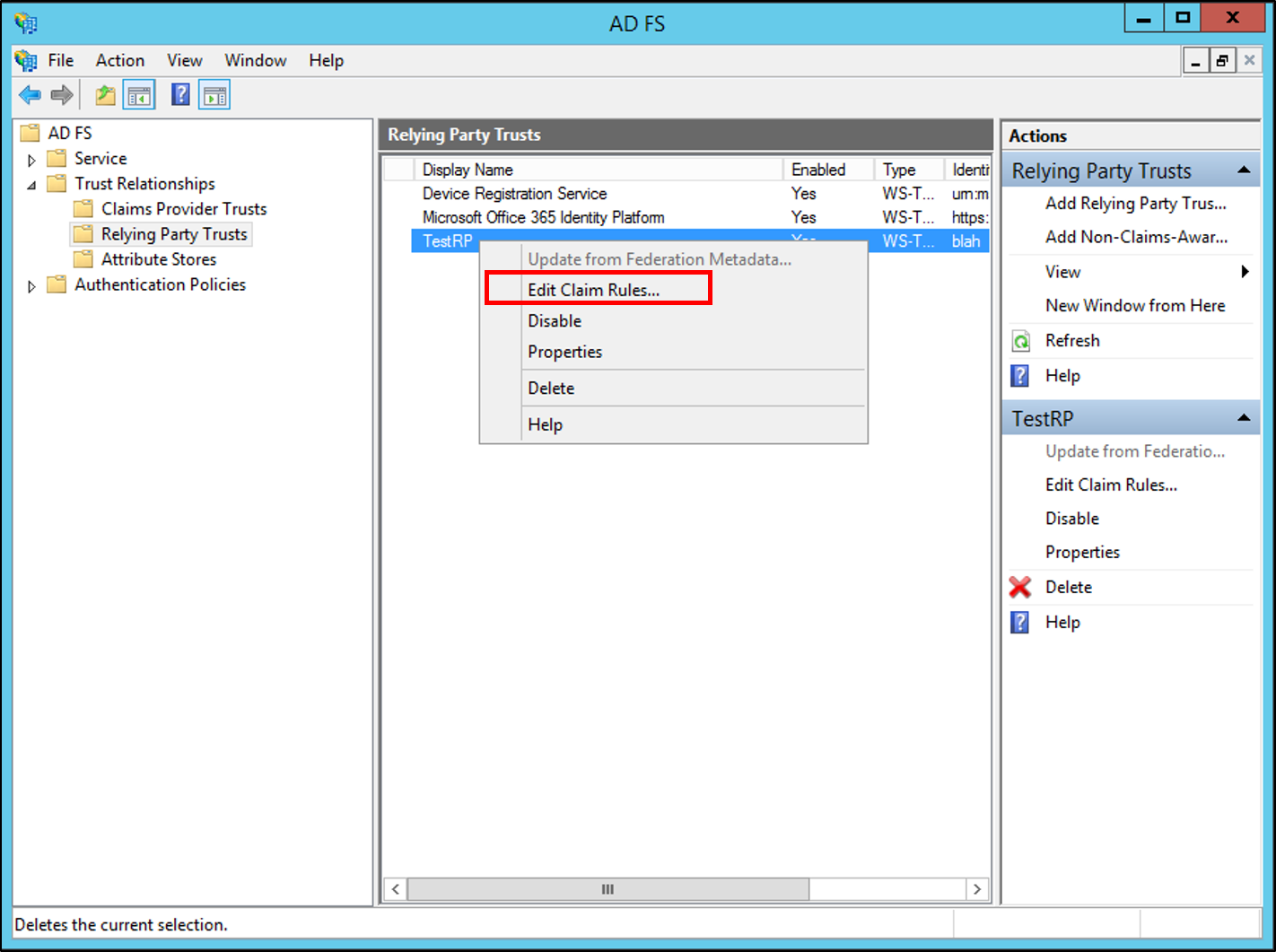
In the Edit Claim Rules dialog box, click the Issuance Authorization Rules tab or the Delegation Authorization Rules tab (based on the type of authorization rule you require), and then click Add Rule to start the Add Authorization Claim Rule Wizard.
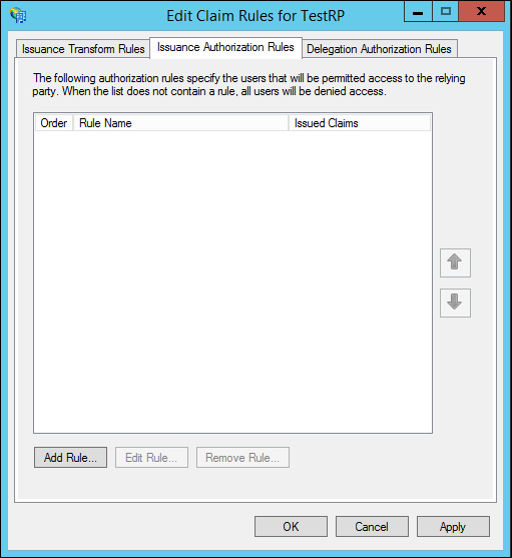
On the Select Rule Template page, under Claim rule template, select Permit or Deny Users Based on an Incoming Claim from the list, and then click Next.
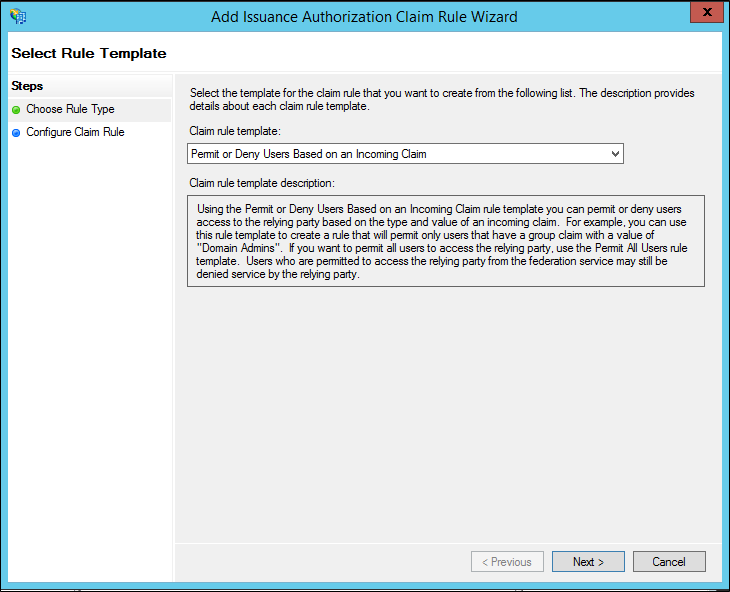
On the Configure Rule page under Claim rule name type the display name for this rule, in Incoming claim type select a claim type in the list, under Incoming claim value type a value or click Browse (if it is available) and select a value, and then select one of the following options, depending on the needs of your organization:
Permit access to users with this incoming claim
Deny access to users with this incoming claim
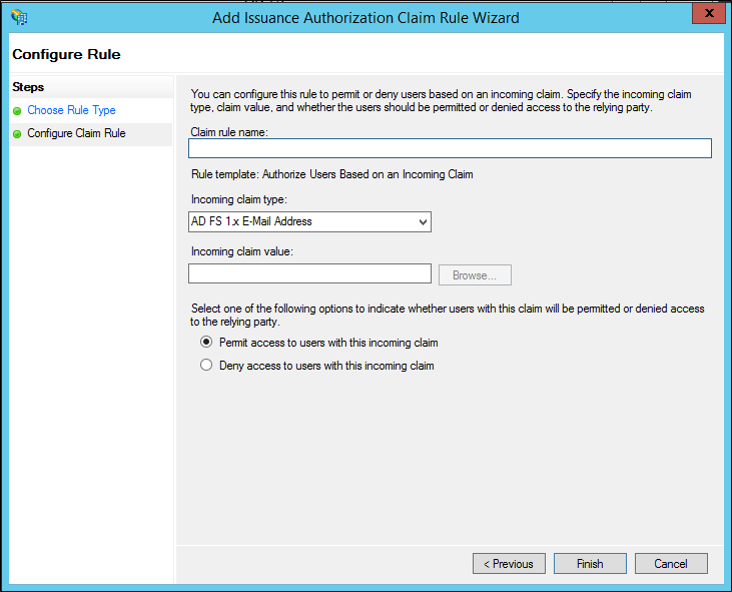
Click Finish.
In the Edit Claim Rules dialog box, click OK to save the rule.
Checklist: Creating Claim Rules for a Relying Party Trust
Events
Apr 29, 2 PM - Apr 30, 7 PM
Join the ultimate Windows Server virtual event April 29-30 for deep-dive technical sessions and live Q&A with Microsoft engineers.
Sign up nowTraining
Module
Create, configure, and manage identities - Training
Access to cloud-based workloads needs to be controlled centrally by providing a definitive identity for each user and resource. You can ensure employees and vendors have just enough access to do their job.
Certification
Microsoft Certified: Identity and Access Administrator Associate - Certifications
Demonstrate the features of Microsoft Entra ID to modernize identity solutions, implement hybrid solutions, and implement identity governance.
Documentation
Create a Rule to Permit All Users
Learn more about: Create a Rule to Permit All Users